Azure DDoS Protection
Author: Ronald Fung
Creation Date: 15 May 2023
Next Modified Date: 15 May 2024
A. Introduction
Distributed denial of service (DDoS) attacks are some of the largest availability and security concerns facing customers that are moving their applications to the cloud. A DDoS attack attempts to exhaust an application’s resources, making the application unavailable to legitimate users. DDoS attacks can be targeted at any endpoint that is publicly reachable through the internet.
Azure DDoS Protection, combined with application design best practices, provides enhanced DDoS mitigation features to defend against DDoS attacks. It’s automatically tuned to help protect your specific Azure resources in a virtual network. Protection is simple to enable on any new or existing virtual network, and it requires no application or resource changes.
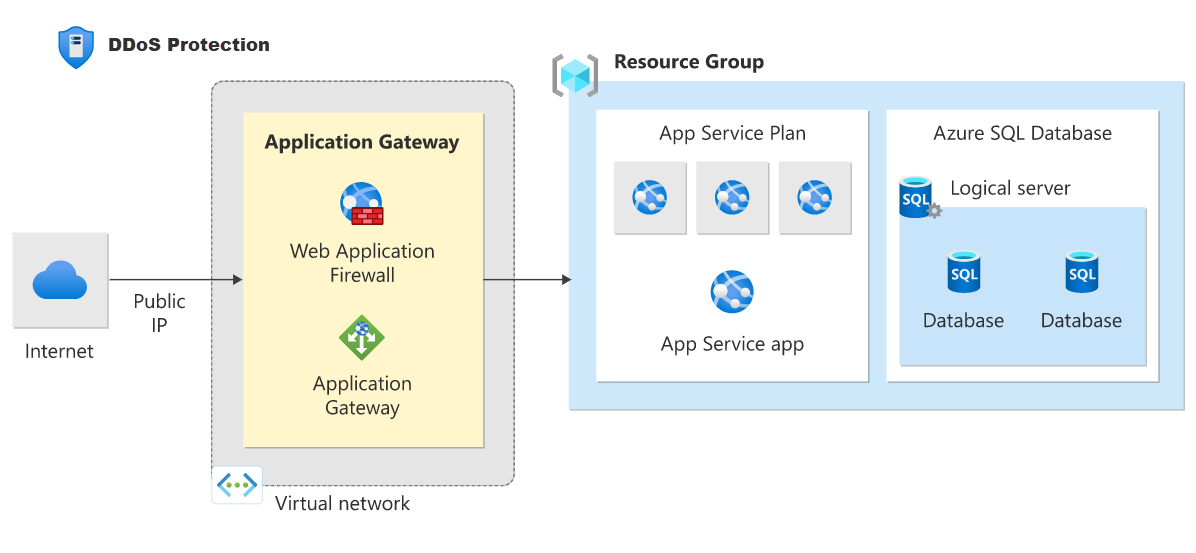
B. How is it used at Seagen
As a biopharma research company using Microsoft Azure, you can use Azure DDoS Protection to protect your applications and resources against Distributed Denial of Service (DDoS) attacks. Here are some ways you can use Azure DDoS Protection:
Detect and mitigate DDoS attacks: Azure DDoS Protection provides detection and mitigation capabilities to help you identify and mitigate DDoS attacks. Azure DDoS Protection Standard uses machine learning algorithms to detect and mitigate DDoS attacks automatically.
Scale protection on demand: Azure DDoS Protection allows you to scale your protection on demand based on your application workload. You can use Azure DDoS Protection Standard to protect your resources at the application layer and network layer.
Monitor DDoS protection: Azure DDoS Protection provides monitoring and reporting capabilities to help you track and report on DDoS protection activities. You can use the Azure portal or APIs to view detailed reports and analysis of DDoS protection activities.
Integrate with other Azure services: Azure DDoS Protection can be integrated with other Azure services such as Azure Load Balancer, Azure Virtual Network, and Azure Application Gateway. This allows you to secure your resources across different Azure services.
Manage DDoS protection policies: Azure DDoS Protection allows you to manage DDoS protection policies and configure protection for your resources. You can use Azure Policy to enforce DDoS protection policies across your Azure environment.
C. Features
Always-on traffic monitoring
Your application traffic patterns are monitored 24 hours a day, 7 days a week, looking for indicators of DDoS attacks. Azure DDoS Protection instantly and automatically mitigates the attack, once it’s detected.
Adaptive real time tuning
Intelligent traffic profiling learns your application’s traffic over time, and selects and updates the profile that is the most suitable for your service. The profile adjusts as traffic changes over time.
DDoS Protection telemetry, monitoring, and alerting
Azure DDoS Protection applies three auto-tuned mitigation policies (TCP SYN, TCP, and UDP) for each public IP of the protected resource, in the virtual network that has DDoS enabled. The policy thresholds are auto-configured via machine learning-based network traffic profiling. DDoS mitigation occurs for an IP address under attack only when the policy threshold is exceeded.
Azure DDoS Rapid Response
During an active attack, Azure DDoS Protection customers have access to the DDoS Rapid Response (DRR) team, who can help with attack investigation during an attack and post-attack analysis. For more information, see Azure DDoS Rapid Response.
SKU
Azure DDoS Protection is offered in two available SKUs, DDoS IP Protection and DDoS Network Protection. For more information about the SKUs, see SKU comparison.
Native platform integration
Natively integrated into Azure. Includes configuration through the Azure portal. Azure DDoS Protection understands your resources and resource configuration.
Turnkey protection
Simplified configuration immediately protects all resources on a virtual network as soon as DDoS Network Protection is enabled. No intervention or user definition is required. Similarly, simplified configuration immediately protects a public IP resource when DDoS IP Protection is enabled for it.
Multi-Layered protection
When deployed with a web application firewall (WAF), Azure DDoS Protection protects both at the network layer (Layer 3 and 4, offered by Azure DDoS Protection) and at the application layer (Layer 7, offered by a WAF). WAF offerings include Azure Application Gateway WAF SKU and third-party web application firewall offerings available in the Azure Marketplace.
Extensive mitigation scale
All L3/L4 attack vectors can be mitigated, with global capacity, to protect against the largest known DDoS attacks.
Attack analytics
Get detailed reports in five-minute increments during an attack, and a complete summary after the attack ends. Stream mitigation flow logs to Microsoft Sentinel or an offline security information and event management (SIEM) system for near real-time monitoring during an attack. See View and configure DDoS diagnostic logging to learn more.
Attack metrics
Summarized metrics from each attack are accessible through Azure Monitor. See View and configure DDoS protection telemetry to learn more.
Attack alerting
Alerts can be configured at the start and stop of an attack, and over the attack’s duration, using built-in attack metrics. Alerts integrate into your operational software like Microsoft Azure Monitor logs, Splunk, Azure Storage, Email, and the Azure portal. See View and configure DDoS protection alerts to learn more.
Cost guarantee
Receive data-transfer and application scale-out service credit for resource costs incurred as a result of documented DDoS attacks.
Architecture
Azure DDoS Protection is designed for services that are deployed in a virtual network. For other services, the default infrastructure-level DDoS protection applies, which defends against common network-layer attacks. To learn more about supported architectures, see DDoS Protection reference architectures.
Pricing
For DDoS Network Protection, under a tenant, a single DDoS protection plan can be used across multiple subscriptions, so there’s no need to create more than one DDoS protection plan. For DDoS IP Protection, there’s no need to create a DDoS protection plan. Customers can enable DDoS IP protection on any public IP resource.
To learn about Azure DDoS Protection pricing, see Azure DDoS Protection pricing.
DDoS Protection FAQ
For frequently asked questions, see the DDoS Protection FAQ.
D. Where Implemented
E. How it is tested
Testing Azure DDoS Protection involves ensuring that the service is functioning correctly and securely, and meeting the needs of all stakeholders involved in the project. Here are some steps to follow to test Azure DDoS Protection:
Define the scope and requirements: Define the scope of the project and the requirements of all stakeholders involved in the project. This will help ensure that Azure DDoS Protection is designed to meet the needs of all stakeholders.
Develop test cases: Develop test cases that cover all aspects of Azure DDoS Protection functionality, including detection, mitigation, and reporting. The test cases should be designed to meet the needs of the organization, including scalability and resilience.
Conduct unit testing: Test the individual components of Azure DDoS Protection to ensure that they are functioning correctly. This may involve using tools like PowerShell or Azure CLI for automated testing.
Conduct integration testing: Test Azure DDoS Protection in an integrated environment to ensure that it works correctly with other systems and applications. This may involve testing Azure DDoS Protection with different operating systems, browsers, and devices.
Conduct user acceptance testing: Test Azure DDoS Protection with end-users to ensure that it meets their needs and is easy to use. This may involve conducting surveys, interviews, or focus groups to gather feedback from users.
Automate testing: Automate testing of Azure DDoS Protection to ensure that it is functioning correctly and meeting the needs of all stakeholders. This may involve using tools like Azure DevOps to set up automated testing pipelines.
Monitor performance: Monitor the performance of Azure DDoS Protection in production to ensure that it is meeting the needs of all stakeholders. This may involve setting up monitoring tools, such as Azure Monitor, to track usage and identify performance issues.
Address issues: Address any issues that are identified during testing and make necessary changes to ensure that Azure DDoS Protection is functioning correctly and meeting the needs of all stakeholders.
By following these steps, you can ensure that Azure DDoS Protection is tested thoroughly and meets the needs of all stakeholders involved in the project. This can help improve the quality of Azure DDoS Protection and ensure that it functions correctly in a production environment.
F. 2023 Roadmap
????
G. 2024 Roadmap
????
H. Known Issues
There are several known issues that can impact Azure DDoS Protection. Here are some of the most common issues to be aware of:
False positives: Azure DDoS Protection can sometimes flag legitimate traffic as malicious, leading to false positives. It is important to tune the service to avoid false positives and ensure that legitimate traffic is not blocked.
Performance issues: If the service is not properly sized, it can impact performance and availability, causing issues with the speed and reliability of Azure DDoS Protection.
Security issues: Security is a critical concern when it comes to Azure DDoS Protection. It is important to ensure that Azure DDoS Protection is secured and that access to the solution is restricted to authorized personnel.
Compatibility issues: Azure DDoS Protection may not be compatible with all platforms, devices, or languages. It is important to ensure that Azure DDoS Protection is compatible with the organization’s existing infrastructure before implementation.
Scalability issues: Scalability issues can arise when scaling up or down the service. It is important to ensure that the service can scale to meet the needs of the organization.
Integration issues: Integration issues can arise when integrating Azure DDoS Protection with other systems and applications. It is important to ensure that Azure DDoS Protection is designed to work seamlessly with other systems and applications to avoid integration issues.
Testing issues: Testing issues can arise when testing Azure DDoS Protection. It is important to ensure that testing is carried out thoroughly and that all aspects of Azure DDoS Protection functionality are tested.
Overall, Azure DDoS Protection requires careful planning and management to ensure that it is functioning correctly and meeting the needs of all stakeholders involved in the project. By being aware of these known issues and taking steps to address them, you can improve the quality of Azure DDoS Protection and ensure the success of your project.
[x] Reviewed by Enterprise Architecture
[x] Reviewed by Application Development
[x] Reviewed by Data Architecture