Azure Web App Firewall
Author: Ronald Fung
Creation Date: 31 May 2023
Next Modified Date: 31 May 2024
A. Introduction
Web Application Firewall (WAF) provides centralized protection of your web applications from common exploits and vulnerabilities. Web applications are increasingly targeted by malicious attacks that exploit commonly known vulnerabilities. SQL injection and cross-site scripting are among the most common attacks.
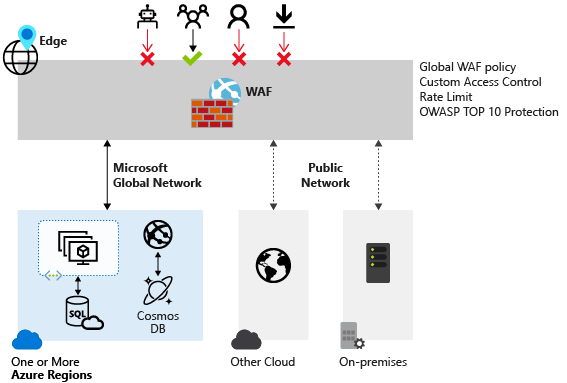
Preventing such attacks in application code is challenging. It can require rigorous maintenance, patching, and monitoring at multiple layers of the application topology. A centralized web application firewall helps make security management much simpler. A WAF also gives application administrators better assurance of protection against threats and intrusions.
A WAF solution can react to a security threat faster by centrally patching a known vulnerability, instead of securing each individual web application.
Supported service
WAF can be deployed with Azure Application Gateway, Azure Front Door, and Azure Content Delivery Network (CDN) service from Microsoft. WAF on Azure CDN is currently under public preview. WAF has features that are customized for each specific service. For more information about WAF features for each service, see the overview for each service.
B. How is it used at Seagen
As a biopharma research company that uses Microsoft Azure, Azure Web Application Firewall (WAF) can be used to provide an additional layer of security for your web applications. Here are some ways that Seagen can use Azure WAF:
Protect web applications: Azure WAF can be used to protect your web applications from common web-based attacks, such as SQL injection and cross-site scripting (XSS).
Custom rules: Azure WAF allows you to create custom rules to block specific types of attacks that may be targeted at your web applications.
Integrated with Azure: Azure WAF is integrated with Azure Application Gateway and Azure Front Door, making it easy to add security features to your existing Azure applications.
Easy to configure: Azure WAF is easy to configure and can be set up in just a few minutes, allowing you to quickly add an additional layer of security to your web applications.
Real-time monitoring: Azure WAF provides real-time monitoring of your web traffic, allowing you to identify and respond to potential security threats as they arise.
Advanced analytics: Azure WAF provides advanced analytics that can be used to identify potential security threats and track the performance of your web applications.
Cost-effective: Azure WAF is a cost-effective solution for securing your web applications, as it does not require any additional hardware or software.
Overall, Azure WAF is a powerful tool for providing an additional layer of security to your web applications. Its ability to protect web applications, custom rules, integration with Azure, easy configuration, real-time monitoring, advanced analytics, and cost-effectiveness make it an ideal solution for businesses looking to secure their web applications from web-based attacks.
C. Features
Azure Web Application Firewall (WAF) is a cloud-based service that provides an additional layer of security for your web applications. Here are some of the key features of Azure WAF:
Protection against web attacks: Azure WAF provides protection against common web-based attacks, such as SQL injection and cross-site scripting (XSS), helping to keep your web applications secure.
Custom rules: Azure WAF allows you to create custom rules to block specific types of attacks that may be targeted at your web applications.
Integration with Azure: Azure WAF is integrated with Azure Application Gateway and Azure Front Door, making it easy to add security features to your existing Azure applications.
Easy to configure: Azure WAF is easy to configure and can be set up in just a few minutes, allowing you to quickly add an additional layer of security to your web applications.
Real-time monitoring: Azure WAF provides real-time monitoring of your web traffic, allowing you to identify and respond to potential security threats as they arise.
Advanced analytics: Azure WAF provides advanced analytics that can be used to identify potential security threats and track the performance of your web applications.
Cost-effective: Azure WAF is a cost-effective solution for securing your web applications, as it does not require any additional hardware or software.
SSL offloading: Azure WAF supports SSL offloading, which can help to improve the performance of your web applications.
Geo-filtering: Azure WAF allows you to block traffic from specific geographic regions, helping to prevent attacks from countries or regions known for cybercrime.
Bot protection: Azure WAF includes bot protection features that can be used to block malicious bots from accessing your web applications.
Overall, Azure WAF is a powerful tool for providing an additional layer of security to your web applications. Its ability to protect against web attacks, custom rules, integration with Azure, easy configuration, real-time monitoring, advanced analytics, cost-effectiveness, SSL offloading, geo-filtering, and bot protection features make it an ideal solution for businesses looking to secure their web applications from cyber threats.
D. Where Implemented
E. How it is tested
Testing Azure Web Application Firewall (WAF) involves verifying that the firewall is properly configured and effectively blocking common web-based attacks. Here are some steps you can take to test Azure WAF:
Verify configuration: Verify that Azure WAF is properly configured and integrated with your web applications.
Test web-based attacks: Test Azure WAF by attempting to launch common web-based attacks, such as SQL injection and cross-site scripting (XSS), and verifying that they are blocked by the firewall.
Test custom rules: Test custom rules created in Azure WAF by attempting to launch targeted attacks that match the custom rules and verifying that they are blocked by the firewall.
Test integration: Test the integration of Azure WAF with Azure Application Gateway and Azure Front Door by verifying that the firewall is properly integrated with your existing Azure applications.
Test real-time monitoring: Test the real-time monitoring capabilities of Azure WAF by monitoring web traffic and identifying potential security threats.
Test advanced analytics: Test the advanced analytics capabilities of Azure WAF by using the analytics data to identify potential security threats and track the performance of your web applications.
Test SSL offloading: Test SSL offloading by verifying that the firewall is properly offloading SSL and improving the performance of your web applications.
Test geo-filtering: Test geo-filtering by blocking traffic from specific geographic regions and verifying that the firewall is effectively blocking access from these regions.
Test bot protection: Test bot protection features by launching malicious bots and verifying that they are effectively blocked by the firewall.
Overall, testing Azure WAF involves verifying that the firewall is properly configured, effectively blocking common web-based attacks, properly integrated with your existing Azure applications, providing real-time monitoring, delivering advanced analytics data, supporting SSL offloading, geo-filtering, and bot protection features. By testing Azure WAF, you can ensure that your web applications are effectively protected from cyber threats and that your business is secure.
F. 2023 Roadmap
????
G. 2024 Roadmap
????
H. Known Issues
As with any software, there may be known issues or limitations that users should be aware of when using Azure Web Application Firewall (WAF). Here are some of the known issues for Azure WAF:
False positives: Azure WAF may generate false positive alerts, which can lead to legitimate traffic being blocked.
False negatives: Azure WAF may not detect all types of web-based attacks, which can lead to security vulnerabilities in your web applications.
Limited customization: Azure WAF may have limited customization options, which can limit the ability of users to create custom rules to block specific types of attacks.
Performance issues: Azure WAF may experience performance issues when processing large amounts of web traffic, which can impact the overall performance of your web applications.
Compatibility issues: Azure WAF may have compatibility issues with certain web applications or programming languages, which can limit the ability of users to use the service with their existing software stack.
Cost: Azure WAF may be more expensive than other web application firewall solutions, which can be a factor for businesses with limited budgets.
Complexity: Azure WAF can be complex to configure and manage, which may require additional training and support for users.
Overall, while Azure WAF is a powerful tool for securing your web applications, users must be aware of these known issues and take steps to mitigate their impact. This may include monitoring and tuning the firewall to reduce false positives and negatives, carefully selecting web applications and programming languages that are compatible with Azure WAF, carefully configuring the firewall to meet the specific needs of their business, providing training and support to users to effectively use and manage Azure WAF, and carefully evaluating the cost and complexity of the solution to ensure that it is a good fit for their business.
[x] Reviewed by Enterprise Architecture
[x] Reviewed by Application Development
[x] Reviewed by Data Architecture