Azure Firewall
Author: Ronald Fung
Creation Date: 17 May 2023
Next Modified Date: 17 May 2024
A. Introduction
Azure Firewall is a cloud-native and intelligent network firewall security service that provides the best of breed threat protection for your cloud workloads running in Azure. It’s a fully stateful, firewall as a service with built-in high availability and unrestricted cloud scalability. It provides both east-west and north-south traffic inspection. To learn what’s east-west and north-south traffic, see East-west and north-south traffic.
B. How is it used at Seagen
As a biopharma research company using Microsoft Azure, you can use Azure Firewall to protect your virtual networks and applications from cyber threats. Here are some ways you can use Azure Firewall:
Secure your network: Azure Firewall allows you to create and enforce network security policies to protect your virtual networks and applications from cyber threats. You can use the Azure portal or APIs to define network security rules and configure security alerts.
Protect your applications: Azure Firewall allows you to protect your applications from unauthorized access and data exfiltration. You can use Azure Firewall Application Rules to define application-level security policies and block traffic that violates these policies.
Monitor network activity: Azure Firewall provides logging and reporting capabilities to help you monitor network activity and identify security threats. You can use Azure Monitor or Azure Security Center to monitor firewall activity and configure alerts for any suspicious activity.
Scale your security: Azure Firewall allows you to scale your security based on your workload. You can use Azure Firewall Premium to handle high-volume traffic and provide advanced security features such as intrusion detection and prevention.
Integrate with other Azure services: Azure Firewall can be integrated with other Azure services such as Azure Virtual Network, Azure Application Gateway, and Azure Load Balancer. This allows you to secure your network and applications across different Azure services and applications.
C. Features
Azure Firewall is offered in three SKUs: Standard, Premium, and Basic.
Azure Firewall Standard
Azure Firewall Standard provides L3-L7 filtering and threat intelligence feeds directly from Microsoft Cyber Security. Threat intelligence-based filtering can alert and deny traffic from/to known malicious IP addresses and domains that are updated in real time to protect against new and emerging attacks.
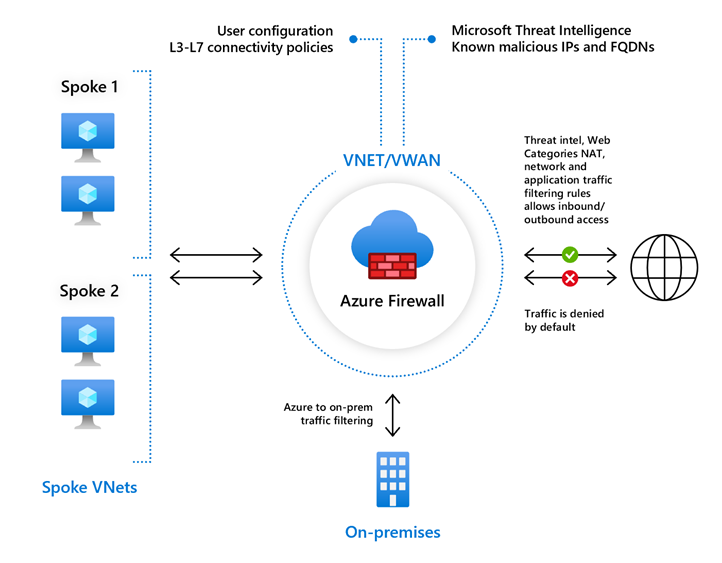
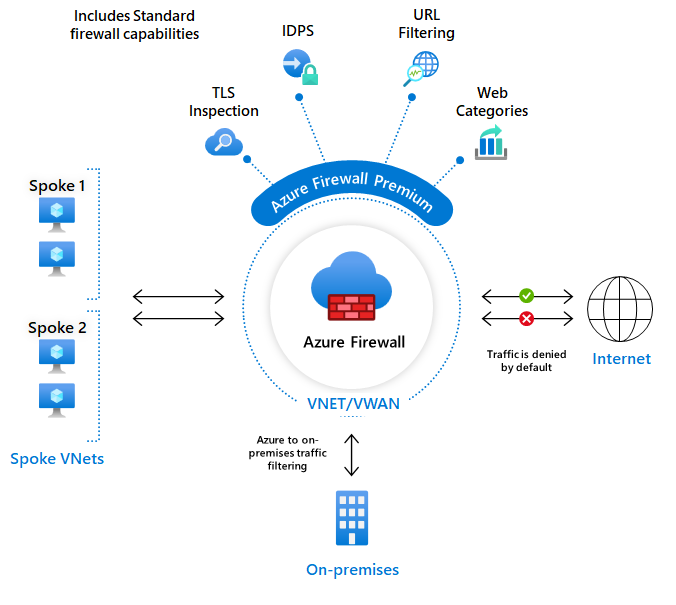
To learn about Firewall Standard features, see Azure Firewall Standard features.
Azure Firewall Basic
Azure Firewall Basic is intended for small and medium size (SMB) customers to secure their Azure cloud environments. It provides the essential protection SMB customers need at an affordable price point.
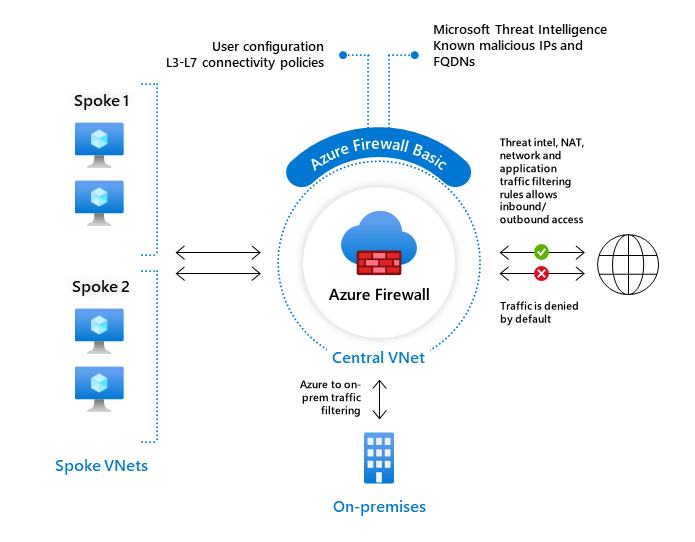
Azure Firewall Basic is similar to Firewall Standard, but has the following main limitations:
Supports Threat Intel alert mode only.
Fixed scale unit to run the service on two virtual machine backend instances.
Recommended for environments with an estimated throughput of 250 Mbps.
To deploy a Basic Firewall, see Deploy and configure Azure Firewall Basic and policy using the Azure portal.
Azure Firewall Manager
You can use Azure Firewall Manager to centrally manage Azure Firewalls across multiple subscriptions. Firewall Manager uses firewall policy to apply a common set of network/application rules and configuration to the firewalls in your tenant.
Firewall Manager supports firewalls in both VNet and Virtual WANs (Secure Virtual Hub) environments. Secure Virtual Hubs use the Virtual WAN route automation solution to simplify routing traffic to the firewall with just a few steps.
To learn more about Azure Firewall Manager, see Azure Firewall Manager.
D. Where Implemented
E. How it is tested
Testing Azure Firewall involves ensuring that the service is functioning correctly and securely, and meeting the needs of all stakeholders involved in the project. Here are some steps to follow to test Azure Firewall:
Define the scope and requirements: Define the scope of the project and the requirements of all stakeholders involved in the project. This will help ensure that Azure Firewall is designed to meet the needs of all stakeholders.
Develop test cases: Develop test cases that cover all aspects of Azure Firewall functionality, including creating and managing firewall rules, monitoring network traffic, and setting up logging and analytics. The test cases should be designed to meet the needs of the organization, including scalability and resilience.
Conduct unit testing: Test the individual components of Azure Firewall to ensure that they are functioning correctly. This may involve using tools like PowerShell or Azure CLI for automated testing.
Conduct integration testing: Test Azure Firewall in an integrated environment to ensure that it works correctly with other systems and applications. This may involve testing Azure Firewall with different operating systems, browsers, and devices.
Conduct user acceptance testing: Test Azure Firewall with end-users to ensure that it meets their needs and is easy to use. This may involve conducting surveys, interviews, or focus groups to gather feedback from users.
Automate testing: Automate testing of Azure Firewall to ensure that it is functioning correctly and meeting the needs of all stakeholders. This may involve using tools like Azure DevOps Pipelines to set up automated testing pipelines.
Monitor performance: Monitor the performance of Azure Firewall in production to ensure that it is meeting the needs of all stakeholders. This may involve setting up monitoring tools, such as Azure Monitor, to track usage and identify performance issues.
Address issues: Address any issues that are identified during testing and make necessary changes to ensure that Azure Firewall is functioning correctly and meeting the needs of all stakeholders.
By following these steps, you can ensure that Azure Firewall is tested thoroughly and meets the needs of all stakeholders involved in the project. This can help improve the quality of Azure Firewall and ensure that it functions correctly in a production environment.
F. 2023 Roadmap
????
G. 2024 Roadmap
Public peering is no longer available on new ExpressRoute circuits and is scheduled for retirement on March 31, 2024.
H. Known Issues
There are several known issues that can impact Azure Firewall. Here are some of the most common issues to be aware of:
Performance issues: Performance issues can arise when Azure Firewall is under heavy load, leading to issues with network traffic and latency. It is important to monitor performance and address any issues that arise.
Compatibility issues: Azure Firewall may not be compatible with all platforms, devices, or languages. It is important to ensure that Azure Firewall is compatible with the organization’s existing infrastructure before implementation.
Security issues: Security is a critical concern when it comes to Azure Firewall. It is important to ensure that Azure Firewall is secured and that access to the solution is restricted to authorized personnel.
Configuration issues: Configuration issues can arise when configuring Azure Firewall, leading to issues with network traffic and connectivity. It is important to ensure that the service is properly configured to avoid these issues.
Deployment issues: Deployment issues can arise when deploying Azure Firewall in a complex environment. It is important to ensure that the deployment process is thoroughly tested and that all dependencies are accounted for.
Logging and Analytics issues: Issues with logging and analytics can impact the effectiveness of Azure Firewall. It is important to ensure that logging and analytics are properly configured and that the data is being properly analyzed.
Licensing issues: Licensing issues can arise when using Azure Firewall. It is important to ensure that the appropriate licensing is in place to avoid any legal issues.
Overall, Azure Firewall requires careful planning and management to ensure that it is functioning correctly and meeting the needs of all stakeholders involved in the project. By being aware of these known issues and taking steps to address them, you can improve the quality of Azure Firewall and ensure the success of your project.
[x] Reviewed by Enterprise Architecture
[x] Reviewed by Application Development
[x] Reviewed by Data Architecture